What happens when you sign in with Microsoft or Google?
You know how it is these days. You install an App or register on a website, and it asks whether you want to sign in with Outlook, Microsoft 365, Google or similar rather than having to remember yet another password. It’s all enticingly convenient. And it seems pretty benign. After all, you can see that it is Microsoft or Google asking you for your password rather than the app, so it’s definitely not identity theft.
Or might you be giving away more than you thought?
Whenever you do this, you are giving the app or website permission to access elements of your account. The permissions granted might be as reasonable as giving it access to your basic profile information (Name, email, etc). But they can ask for a whole lot more. Only you stand in the way of them getting total access to your email, contacts, calendar and other sensitive elements of your digital life.
A example to bring the issue to life
Let me use the Shopify ‘Shop’ app as an example. I’ve selected it only as an illustration because it came to my attention recently. A broad range of other apps and services are undoubtedly adopting similar practices.
At Digility we use Microsoft 365 (this fact is easy to discover with a cursory DNS search, so please hold back on the comments accusing me of over-sharing). The other day our Marketing Manager leant across with a concerned frown. She was registering with the Shop app to track a purchase she had just made, and it had asked her to connect her Microsoft 365 account. She showed me the screen displaying the permissions the app was asking her to grant, concerned that it was asking for quite a lot.
What are they asking for?
You can see from the picture below that it is requesting three things.
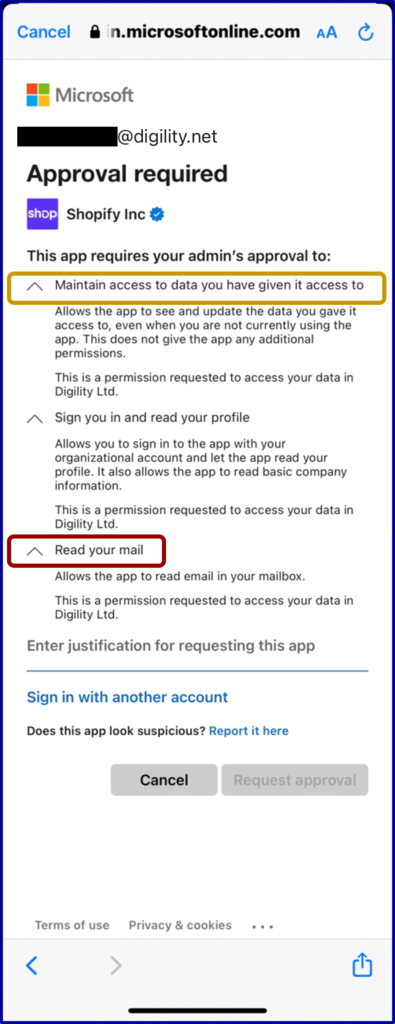
The middle one, “Sign in and read user profile”, is the least concerning. This lets the app allow Microsoft to confirm who you are and get basic identity information about you.
We were a little concerned about the top one, which asks to “Maintain access to data you have given it access to”. You would be allowing the app to continue using the permissions you gave it even when you aren’t there. If you haven’t been overgenerous in the permissions granted this may be tolerable. And we have found that even when an app doesn’t ask for this “offline access”, Microsoft still seems to grant it, so it might be unavoidable. But I’d still prefer to be in control unless I wanted the app to be accessing things on a 24/7 basis.
It was the last permission that rang serious alarm bells, though. They were asking to “Read user email”. I’ll ask a simple question. Do you want an app that exists only to notify you if a purchase is about to be delivered to be able to read every email you have sent or received?
Why do you need to be concerned?
That seems like overkill to me in a personal context. You might feel you can trust Shopify not to read through your emails (though I wonder if I would). But how confident are you that their security is sufficient to prevent someone hacking them to access all of their customers’ connected accounts? Or how sure are you that an employee couldn’t be persuaded to put in a back door? To be clear, I’m not suggesting that their security is weak; I simply don’t know and therefore have no basis for trust.
But in a business context, this is very bad. Never mind your company’s sensitive information being made available to a third party with no due diligence and little contractual protection. Approving this app will breach the NDAs and confidentiality clauses you have in place with customers, clients and partners. It will undoubtedly break numerous privacy laws. And depending on the business’s situation, it may also contravene various market regulations.
Most established businesses and those with good security practices will have prevented users from approving this type of app themselves. They will have configured their services so that only an administrator can approve it (as you can see is the case with us). But there will be a lot of small and medium-sized businesses out there who are unaware of the damage that can be done by enabling a little convenience.
You can control this in Microsoft 365 in the User Consent Settings section of the Azure Portal. We would recommend that you set this to not allow user consent, and to always require an administrator to approve it. To make it easier for the user you should then allow users to request consent in the Admin Consent Settings and specify the people or groups that these requests are sent to.
Google Workspace does not currently let you apply a similar proactive global policy, except for educational subscribers to protect minors; this is quite a significant security weakness.
Summary
So next time you sign in with Google or Microsoft, do check what the service is asking you to approve. Ask yourself whether you are comfortable for a total stranger to have access to that type of information.
Personally, I’ll pass on this order-tracking app. That is a personal decision, and you may have a different attitude to the risk. But risk, whether personal or business risk, needs to be a considered decision rather than just a box-ticking (or button-clicking) exercise.





